HIPAA Audit

We understand that in today’s world, cyber security is simply not an option; it is a mandate. Security helps to preserve citizen trust by mitigating the risk of unauthorized use or loss of sensitive information. Today’s increasingly interconnected Information Technology (IT) infrastructure is under the continual increasing threat of unauthorized access. As more and more sensitive citizen data is collected, stored, used, and shared each day, a strong security risk management approach is necessary to comply with the Federal, Internal Revenue Service (IRS), and other key regulatory statutes such as the Health Insurance Portability and Accountability Act (HIPAA). The increasing sophistication of cyber-attacks and publicized data breaches in the state sector further underscore the importance of a strong security posture and risk management approach.
In addition, increased enforcement and penalties resulting from the HITECH Act have caused many organizations to revisit their readiness to address the HIPAA Privacy and Security Rules as well as those changes proposed by the HITECH Act.
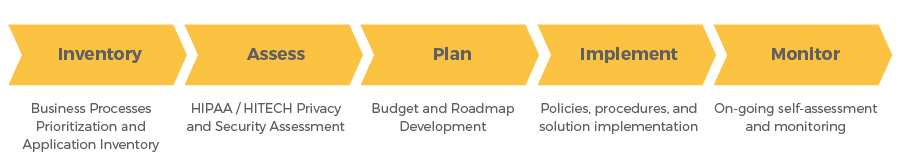
The following describes WeSecure’shigh level approach for undertaking anHIPAA assessment and security implementation project.
- Inventory and prioritize business processes and applications to identify areas of focus
- Identify the “real issues” that may affect the organizations’ ability to address HIPAA
- Work with key IT and business stakeholders to assess and prioritize risks to the organization
- Establish implementation budget, schedule, and program management structure
- Select and implement administrative, physical, and technical solutions based on risk prioritization
- Enable an HIPAA sustainment and self-monitoring process
Ask Yourself:
- Does the organization need to understand where the protected health information is stored or transferred?
- Are the organization’s privacy and security policies and procedures out of date?
- Does the organization have difficulty in listing out all third parties with whom it may share patient or health benefit participant information?
- Establish implementation budget, schedule, and program management structure
- Select and implement administrative, physical, and technical solutions based on risk prioritization
- Is the organization a Business Associate or a service/solution provider of a Covered Entity?
- Has the organization encountered a breach of protected health information recently?
If you have answered “Yes” to any of these questions, it may be time to consider a HIPAA Assessment.
Low Level Approach
Like any healthcare organization in the industry, any healthcare organization would utilize information technology across all its operations to manage the patient, finance, personnel, vendor and customer data across multiple departments and locations. For such organization’s we provide leading services to conduct an enterprise wide HIPAA privacy and security assessment and audit to:
- Identify where PHI resides,
- Identify potential control gaps comparing its existing controls to the HIPAA privacy and security requirements, and
- Recommendation solution for mitigating the gaps.
Phase One – Business Processes Prioritization and Application Inventory
This phase emphasizes on identifying the business processes and supporting applications that involve the collection, use, and storage of PHI in connection with thecorresponding client – lines of business (LOBs) and prioritize the business processes for the subsequent assessment and planning activities using the risk criteria approved by client management.
Phase Two – HIPAA Privacy and Security Assessment
For the selected high-risk business processes and supporting applications/systems, this phase focuses on assisting the client with the identification of potential control gaps that may exist in their business and IT, and operating environment by comparing organization’s existing business processes and privacy and security controls against the HIPAA Privacy and Security Rule requirements.
Phase Three – Remediation Plan Development
This phase concentrates on assistingthe organization with the development of remediation options and assembling remediation plans to address identified control gaps, including quantifying the timeline requirements for each remediation project, and designing a remediation roadmap considering individual project schedules and synergies with other projects.
Phase One: Business Processes Prioritization and Application Inventory
The purpose of this phase is to identify the business processes and applications that collect, use, or store PHI. These business processes and supporting applications currently exist within the organization’s lines of business. Key activities during this phase will include:
- Confirm with the client the services from which business processes will be inventoried and prioritized and confirm the key business/IT contact for each of the included services.
- Prepare the PHI business process and application inventory survey to be distributed to the key contact for each of the included lines of business. WeSecure will work with the client to identify if we can use our automated processes to assist with the PHI survey process.
- Confirm with client the risk criteria that will be used to prioritize the business processes, control gaps, and remediation activities. As per our vast experience across healthcare, we have developed our own risk matrixes. The focus would be to get both parties agree upon the identified business process risk criteria prior to the business process prioritization exercise
- Prioritize the business processes and applications using the pre-approved risk criteria and select the high-risk business processes and supporting applications/systems for subsequent assessment and planning activities.
Key deliverables from Phase One will include an Excel spreadsheet capturing the current PHI business processes and application inventory.
Phase Two: HIPAA Privacy and Security Assessment
The purpose of this phase is to identify control gaps for the selected business processes and applications/systems by comparing organizations existing business processes and privacy and security controls against the HIPAA Privacy and Security Rule requirements. Key activities during this phase will include:
- Under the HIPAA Privacy Rule, assess the selected business processes by comparing the organization’s existing privacy controls to the HIPAA privacy requirements as they relate to administrative requirements, uses and disclosures, individual rights, and requirements for business associates.
- Under the HIPAA Security Rule, assess the selected applications and supporting common IT infrastructure components (e.g., network devices, server platforms) by comparing organization’s existing security controls to the HIPAA Security Rule requirements, the HITECH Act requirements, and the HITRUS
- Assessment activities will be primarily performed by documentation reviews and interviews with key business and IT personnel (e.g., representatives from Privacy Office, lines of business, Information Security, Human Resources, application support staff, IT infrastructure support staff, Physical Security, General Counsel, Chief Compliance Officer).
- Compiling a list of HIPAA privacy and security control gaps, including the description of each control gap, the impact to the organization, and the risk ranking of each control gap.
Key deliverables from Phase Two will include a detailed technical report capturing the current control practices and HIPAA privacy and security control gaps.
Phase Three: Remediation Plan Development
The purpose of this step is to develop remediation plans for privacy and security control gaps based on the results from the HIPAA Privacy and Security Rule Assessment. Key activities will include:
- Grouping control gaps into remediation projects based on the types and nature of privacy and security solutions (e.g., policies, standards, and procedures, including breach notification, training and awareness, technical control implementation, improvement to business associate agreement management process).
- Collaborating with business and IT functions to identify project risks and constraints (e.g., competing project timeline, limited resources) and document these risks and constraints. This also includes working with related project teams to understand potential synergies with other business and IT projects, which may be leveraged to address the control gaps identified.
- Prioritizing recommended projects into a phased remediation roadmap, including timing and duration of projects, as well as inter-dependencies.
Key deliverables from Phase Three will include the Executive Summary report, HIPAA privacy and security remediation summary aligned against the HITRUST CSF, and a phased HIPAA privacy and security remediation roadmap.
Our Qualifications
From “HIPAA One” to the recent HITECH Act, EyeD has assisted clients to assist with their HIPAA privacy and security efforts. We had served major payer and provider organizations across multiple areas in their HIPAAassessment and other security audit programs.
- XX+ practitioners in the United States dedicated to the information security, privacy, and data protection
- Real-life experience in HIPAA privacy and security compliance implementation with up to date knowledge in HITECH
- HITRUST CSF Assessor having wide experience providing services for the Common Security Framework (CSF), incorporating the existing security requirements of healthcare organizations
- Customized field tested methodologies and tools aligned with industry standards for supporting HIPAA implementation (e.g., Survey Portal with built in HIPAA privacy and security content, NIST/HIMSS aligned application security survey)
- Seasoned security and privacy specialists focusing on the healthcare space with over a dozen HIPAAprojects delivered in the past year and half
- Deepunderstanding of challenges faced by healthcare clients in HIPAA privacy and security remediation; served as HIPAA program PMO and technical lead; assisted executive communications for HIPAA program and success metrics

