Security Operations Center (SOC)
To maximize the SIEM investment and increase business value for the organization just depending on a SIEM vendor would not help. But also should adopt a well thought-out strategy, an enterprise vision, and a roadmap to address their tactical, strategic and operational needs and hence increase their security posture. We understand that a SIEM integrated with the infrastructure contributes to working as a vital tool for managing the complete Security Operations in an organization and thus transcend towards Managed Services.
Key Drivers for Security Operations Center
External and internal business drivers are demanding more transparency into system and application access activities. Effectively managing IT risk and compliance monitoring requirements by focusing on what matters most is the need of the hour.
Compliance and Reporting: Need for the ability to monitor and report access activities to key financial data and consumer personal information (e.g. PCI, HIPAA, SOX).
Incident Investigation: Need for the ability to collect and analyze security and correlate them to identify the root cause of an incident.
Event Correlation: Need for the ability to collect and correlate event data, vulnerability data and configuration data.
Security Effectiveness: Need for the ability to analyze the effectiveness of the security and privacy safeguard. This includes consolidation of disparate event / incident monitoring capabilities to improve operational efficiency.
Managed services to address today’s cyber threat challenges
We believe that a co-sourcing model provides higher value than traditional managed security services provider (MSSP) offerings
Monitor deep within the perimeter using rich internal data sources for better detection of targeted attacks and insider threats.
Keep control of your data and future sourcing options
Evolve monitoring capabilities as your program matures, from compliance, to advanced loss prevention and anomaly detection
Get tailored, specialized support where you need it — from routine systems management and maintenance, to advanced incident analysis and threat research support.
Leverage diversity and depth of skills that would likely be cost-prohibitive to hire as in-house staff
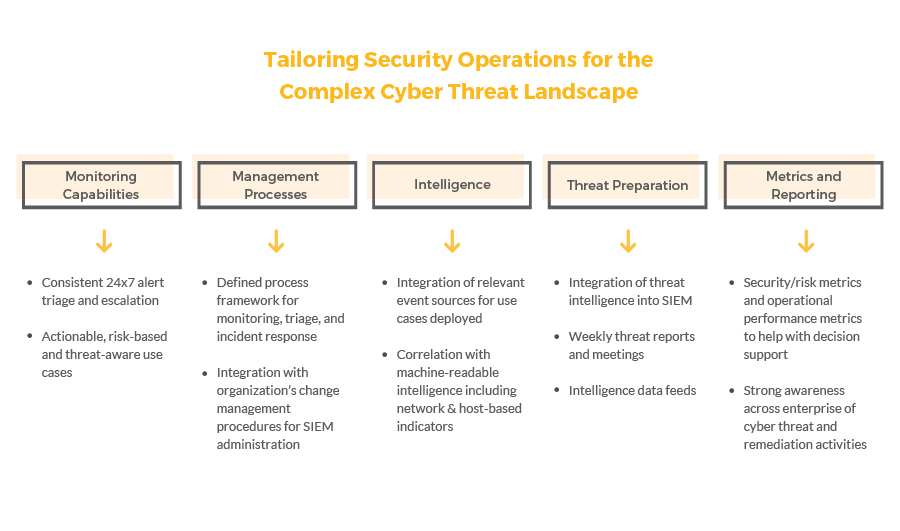
How EyeD Helps You Get There
The accelerated maturity of an organization’s security monitoring is dependent on building security processes, effectively leveraging existing technologies, and building an experienced team to manage it. Outlined below is a two phased approach to help organization’s enhance their security monitoring and risk management capabilities.
Transform
Implement SIEM Enterprise Security: This accelerates monitoring and provides organization pre-built security dashboards, alerts and searches
Implement use cases: Leverage an agile, risk-based methodology to develop actionable SIEM security use cases
Integrate intelligence feed: Enhance the capabilities of the SIEM Through our Threat Intelligence – feed integration and use case implementation to detect and mitigate threats
Define process framework for triage and response: Establish documented processes for core alert triage and incident response activities
Operate
Monitoring 24×7: Perform SIEM alert triage and analysis on a 24x7x365 basis, identify false positives, and escalate potential incidents to incident responders. Leverage operations run books to support operations activities.
SIEM Operational Health Monitoring: Manage 24×7 SIEM operational health monitoring for stability and performance
Documentation: Provide regular reporting on detected threats and key performance monitoring indicators
Collaborate: Interact and work with an organization as an extension of their security team
Our approach to maintenance and operations include the following:
- Provide full lifecycle services related to technology risk infrastructure, spanning the continuum, from upfront advisory services through process/technology implementation, managed security services, improvement, and innovation
- Deliver a team comprising experienced professionals specialized in cyber threat management as well as developing and operationally supporting security monitoring technology
- Leverage extensive relationships with major security vendors, including HP ArcSight, RSA, and IBM
- Given that security monitoring systems are not a one-time, static deployment, follow a continuous development model to address and account for:
- Changes in the internal IT environment—new devices, applications, or technologies that need to be integrated into the organizations overall security strategy
- Changes in the threat landscape or regulatory requirements
- Changes to the security program business drivers
- Bring extensive insight in security operations support that will allow an organization to benefit from active system tuning, maintenance, and capacity planning across multiple platforms, environments, and threat scenarios
- Perform operational analysis in parallel to other monitoring with no interruption to these services. WeSecure analysts review an aggregation of system performance indicators, alerts, reports, and client feedback and report the results in regular checkpoints to the organization.
Security Incident Response Services
Our approach includes:
- Act as the first line of response for security incidents, working with the organization’s Security team to assess declared incidents and help coordinate and execute Security Incident response activities
- Include team members who are multidisciplinary investigative specialists that can conduct and actively assist in analysis, containment, eradication, and recovery.
- Through Threat Intelligence Research, observe, reverse engineer, and anticipate future adversary behaviour and strategies, so that resulting insight can be used to guide defence and prevention activities and programs
- Perform higher order event analysis by reviewing intrusion attempts to look for indicators of compromise, and review packet analysis results to make recommendations for monitoring policies and signatures in security monitoring toolset
SIEM Implementation and Deployment
Implement SIEM Enterprise Security application to enable enriched dash-boarding and monitoring functionality.
Key Activities
- Develop foundational SIEM requirements (technical and business), design and expansion plan
- Install and configure SIEM and Enterprise Security
- Initiate source log data integration
- Enable Correlated Searches, Alerting and Reporting
- Align current processes with industry standard practices
- Transition to Operations and on-going development
24x7 Threat Monitoring
Perform SIEM alert triage and analysis on a 24×7 basis, identify false positives, and escalate potential incidents to the organization’s incident response team
- Plan and develop work stream timeline – Define deadlines, identify stakeholders and set up team access to client SIEM and integration with organization’s ticketing system
- Integrate threat feeds and create use case corresponding to the threat feed package
- Initiate threat monitoring for two-week, 8 hours per day for 5 days (8×5) trial period to test monitoring procedures, ticketing integration, and escalation paths prior turning up 24 * 7 monitoring
- Develop Alert Matrix based on observed security events outlining event types, criticality, associated service level agreements (SLAs), and contact details.
- Turn up 24×7 monitoring, including incident escalation processes, shift scheduling, and weekly threat analysis and SLA reporting
- Define continuous improvement process for SIEM content tuning, false positive mitigation, and SIEM content development feedback cycle
SIEM Operations Health Monitoring and Reporting
Perform SIEM operations health monitoring to confirm that the SIEM platform is functioning as designed
- Plan and develop work stream timeline – Define timelines and identify stakeholders
- Identify established reporting capabilities – Identify automated reporting tool and data feeds
- Identify key stake holders – Identify what stakeholders will be using, maintaining, and enhancing the system
- Implement SIEM Health Monitoring package on the client’s infrastructure
- Enable continuous monitoring and automated alerting on system issues that could impact SIEM operations stability, capacity or performance
- Remediate identified SIEM system issues as part of change management and configuration management data base (CMDB) processes
- Provide weekly and monthly reporting on SIEM system performance
- Define continuous improvement process for SIEM content tuning, false positive mitigation, and SIEM content development feedback cycle
EyeD is Qualified to Serve Because of
Proven industry experience: We have decades of hands-on experience in assisting global manufactures/distributors in designing, implementing, and executing their security programs, enabling us to provide leading practices and lessons learned to multiple organizations. We have performed over xxcyber security projects in the US alone over the past year, with many engagements focused on security operations.
The right approach with the right team: We have over xx security and risk management professionals globally who have worked on a multitude of security program development projects. The proposed team as part of any proposal is comprised of highly qualified specialists, many of whom have implemented and operated highly sophisticated security operations programs, bringing experienced insights from other large, complex organizations.
Methods and tools to accelerate deliverables: WeSecure is a forerunner in the area of security monitoring via SIEM, offering multiple years of direct, relevant experience to organizations. Our team will be equipped with specific intellectual capital and tested tools that help accelerate projects. These allow us to work efficiently, focus our discovery efforts on client specific challenges and consistently deliver high-quality work products.

