-
Enterprise Application Security
-
Key Business Drivers for Enterprise Application Security
-
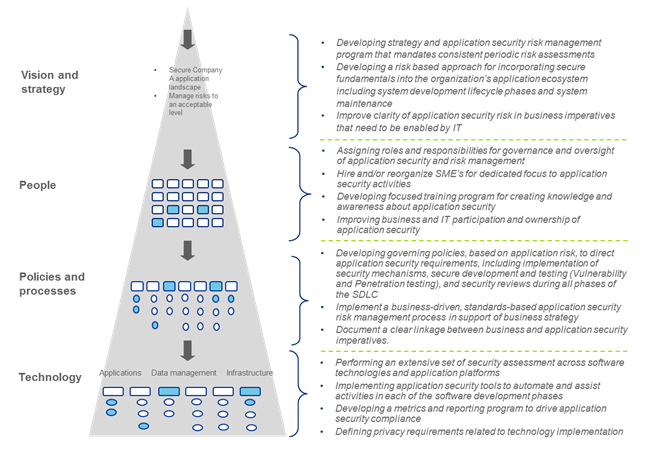
Enterprise Strategy for Application Security
-
Common Technical Application Security focus areas
The business software ecosystem has evolved in todayto the point wherein organization’s sensitive data is no longer safe without comprehensive implementation of an Application Security program. Building aneffective Application Security program starts with learning the discipline’s fundamentals and understanding the different technologies and services available or provisioned by an organization. Security teams that are educated in these areas will be able to make well-informed decisions on how they should design and grow their Application Security programs.
Due to the highly-integrated nature of enterprise applications, the design of security must provide an efficient and effective structure that supports integrity, accuracy, and availability of information without any misuse. Multiple areasmainly from software procurement and development to designing and building the stack of application platform and infrastructure should be covered overall with the overall strategy.
Enterprise Application Security should also focus on business related areas such as strategy towards the technical aspects associated with independent modules and features provisioned by the applications. A comprehensive Enterprise Application Security Strategylargely address an organization’s application development or software policies and procedures, new workflow requirements, and regulatory and compliance mandates.
The following items are primary business drivers for an organization to mature its Application Security program and conduct risk assessments on a regular basis:
Sustainable Software Security & Delivery:The goal of a sustainable application security program is to incorporate software security practices that balance the organization’s security objectives (policies) and corresponding business applications from a flexibility and stability perspective, without introducing unnecessary risk. An enterprise can achieve this goal through the development of a set of actions, methods, processes, and controls, and applying these components systematically within the application procurement and software development life cycle beginning with the conceptualization of the overall application security as a project.
Sustainable Software Security & Delivery:The goal of a sustainable application security program is to incorporate software security practices that balance the organization’s security objectives (policies) and corresponding business applications from a flexibility and stability perspective, without introducing unnecessary risk. An enterprise can achieve this goal through the development of a set of actions, methods, processes, and controls, and applying these components systematically within the application procurement and software development life cycle beginning with the conceptualization of the overall application security as a project.
Data Sharing & Interconnectivity:Enterprise applications usuallyutilizes or provisions advanced digital resources and services, sharing information with their customers every day. Understanding how an enterprise application interconnects with external and internal environments and data protection controls put in place to protect and monitor the efficiency of these controls is one of the key priorities for any business and their customers.
Key Application Security Principles
- Minimize Attack Surface
- Defence in Depth
- Least Privilege
- Establish Secure Defaults
- Fail Securely
- Avoid Reliance on Obscurity
- Keep Security Simple
- Never Trust External Systems
- Compartmentalize
- Detect Intrusions
Data Validation
- Possible attacks: Client Side Injection, Insecure File Upload, Server Side Injection etc.
- Purpose: Process of verifying each input/ output given to/going out of the application.
- Impact: High potential for data leakage, unauthorized access
- Type: Input and output validation
- Key Secure Practices:Indirect selection, white listing, black listing
Error & Exception Management
- Possible attacks: Internal server path disclosure, Stack Trace revealed, Database error pattern
- Purpose: Exception handling is a process of ensuring that all application related errors are handled within the application and appropriate steps are taken to facilitate the normal flow of an application.
- Impact:Improper error and exception management can lead to the disclosure of sensitive information.
- Key Secure Practices:Exception should be specific enough to point out the cause of the exception, log an error code instead of entire details of error/exception.
Auditing & Logging
- Possible attacks: Log forging, Information leakage, Log injection
- Purpose: Auditing and Logging are most effective detective approach to detect a security breach. It can be used to monitor and maintain an application.Auditing and Logging are most effective detective approach to detect a security breach. It can be used to monitor and maintain an application.
- Impact:Lack of proper logs makes it difficult to track the source and operations performed on a database object or other data store.
- Key Secure Practices:Logging and auditing different events, Login events, Request for access, Approval rejections, change of access permissions, Logout events, Access termination events, Log any error and exception
Authentication & Authorization
- Possible attacks: Authentication bypass, Insecure direct object reference, Privilege escalation etc.
- Purpose:
- Authentication is the process of confirming the identity of a person who is attempting to access an application or other information resources database
- Authorization is the process of assigning and verifying user privileges to access protected resources.
- Impact:Lack of sufficient authorization checks leads to privilege escalation, unauthorized access to sensitive information and application functionality.
- Key Secure Practices:Control access to applications and information resources, Trust between multiple parties to communicate with them, Use a centralized access control database, Role base access control.Access Certification, HR event based access certification
Session Management
- Possible attacks: Session fixation, Cross site request forgery, Session hijacking etc.
- Purpose:To keep track of a user’s activity across sessions of interaction with the application. Since HTTP is a stateless protocol it does not maintain user state across subsequent requests
- Impact:Improper session management can lead to stealing of sessions and duplicating sessions illicitly.
- Key Secure Practices:
- Use of a strong method for generating random unique identifiers through a cryptographically strong algorithm for an authenticated user
- Invalidate session at the server side when the user logs out
- Define session time out for applications. Inactive user sessions should be automatically terminated after a reasonable amount of time
- Do not send session identifiers as a query string parameter
Cookie Management
- Possible attacks: Insecure client side data storage, Missing HTTP Only / Secure flags etc.
- Purpose:To handle user preferences and are used to identify the authenticated user’s requests from a client to the server. Cookie management is used to ensure that cookies used in the applications are managed in a secure way.
- Impact:Cookies can be stolen and can be used to recreate a session without logging in.
- Key Secure Practices:
- Ensure that the user session cookie does not contain sensitive.
- Use HTTPOnly and Secure flags on the session cookies. Secure flag prevents the session cookie to be transmitted over insecure channels such as HTTP. This would prevent session hijacking vulnerability.
- Proper input validation must be performed on all cookie parameters.
- The expiry date of persistent cookie must be set for a short duration of the time.
- Implement domain-specific cookies.
Configuration management
- Possible attacks: HTTP banner fingerprinting, Local file inclusion, Directory listing etc.
- Purpose:Configuration management deals with various application configuration attributes which assist the application to be developed and deployed in a secure manner
- Impact:: Improper configurations leads to loopholes in access control, improper exception handling, improper logging etc.
- Key Secure Practices:
- Create a hardening guideline for your particular web server and application server configuration. The hardening guideline should include the following topics:
- Configuring all security mechanisms
- Error handling
- Turning off all unused services
- Setting up roles, permissions, and accounts, including disabling all default accounts or changing their passwords
- Logging and alerts
- Patch management
Data Encryption
- Possible attacks: Weak encryption ciphers support, Unencrypted sensitive data
- Purpose: Data encryption involves encoding a message in such a way that an attacker is not able to decode it, but the application can.
- Impact:Data transferred via plain text is visible directly to any attacker and hence is vulnerable. Confidential information can hence be compromised
- Key Secure Practices:
- Encrypt, hash, or mask the remaining sensitive data at rest and in transit.
- Use built in encryption techniques for Data at Rest or externally encrypt data using leading cryptographic algorithms Data in Motion can be secured using SSL, HTTPS etc.